Home » EDR
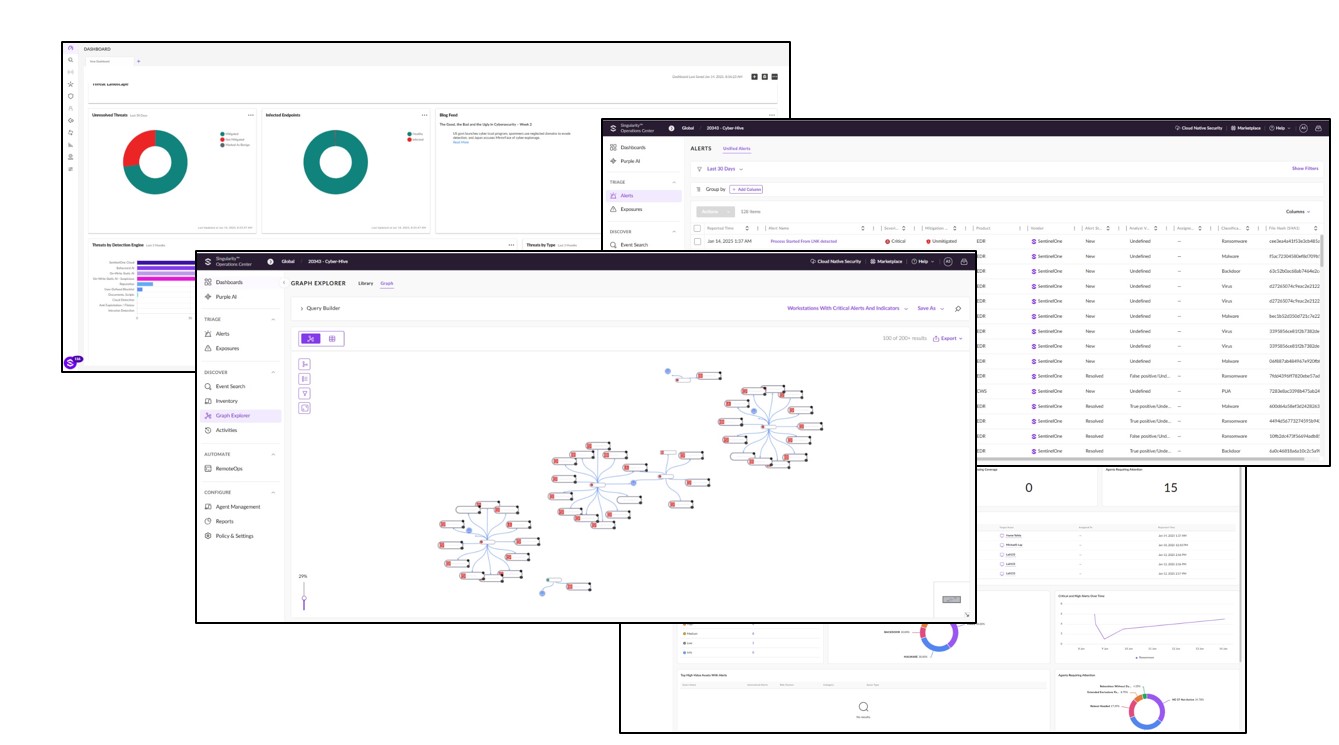
Endpoint Detection and Response (EDR) is a security solution that continuously monitors endpoints (like laptops, desktops, and servers) for suspicious activity, providing real-time insights and response capabilities to detect, analyze, and mitigate cyber threats. EDR solutions are vital for identifying advanced threats and reducing response times in your organization’s security strategy. Here’s how EDR can add value:
What Can You Expect?












